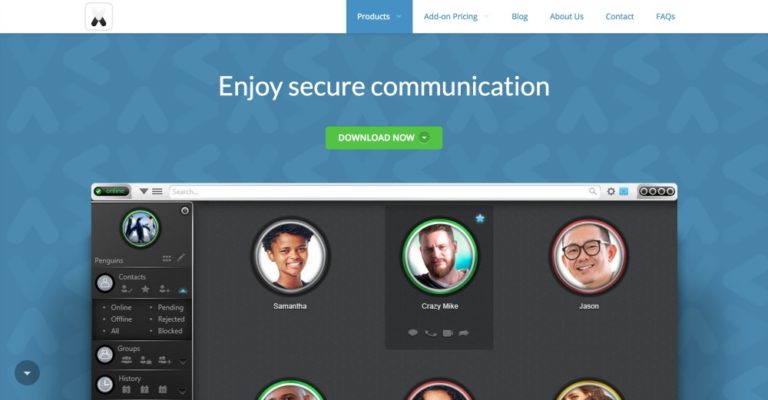
Ed: Todays pitch is a fundamentally great idea, however the thing that would scare the hell out...
Encryption
Regular readers will recall, I am keen for solutions which offer private citizens the option to protect...
goTenna is a new class of internet-less comms device that doesn’t need the internet or the...